Internal dashboards and analytics platforms like GA4, BigQuery, and Looker often contain sensitive customer and business data, but access control is rarely treated as a priority. In many e-commerce setups, team members, agencies, or contractors gain broad visibility into reports and tables they shouldn’t see.
✅ 5 Key Takeaways
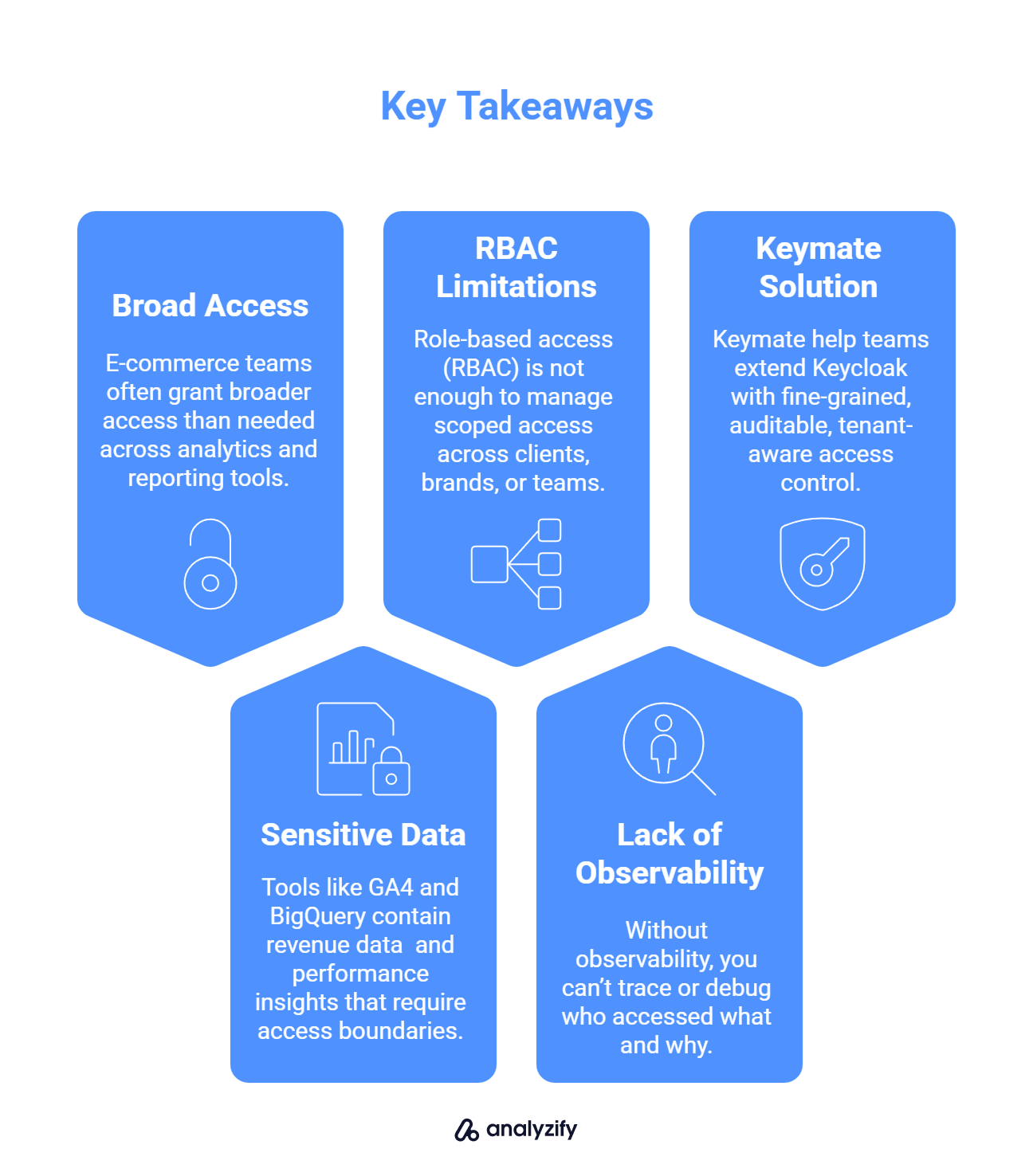
E-commerce teams often grant broader access than needed across analytics and reporting tools.
Tools like GA4 and BigQuery contain PII, revenue data, and performance insights that require strict access boundaries.
Role-based access (RBAC) is not enough to manage scoped access across clients, brands, or teams.
Without observability, you can’t trace or debug who accessed what and why.
Solutions like Keymate help teams extend Keycloak with fine-grained, auditable, tenant-aware access control.
E-commerce Data Tools Often Expose More Than You Think
Many e-commerce companies use internal platforms to centralize and report on business data. These include:
- GA4 for traffic and conversion tracking
- BigQuery as a cloud data warehouse storing raw order and customer data
- Looker Studio for custom dashboards shared across departments or teams
- Internal admin tools for store management, inventory, or order operations
These systems may seem “safe” because they’re internal. But they’re often integrated across departments, shared with external vendors, or linked into client-specific workspaces with little to no access governance.
What Kind of Data Is At Risk?
Even when access is unintentional, the content being exposed is often critical:
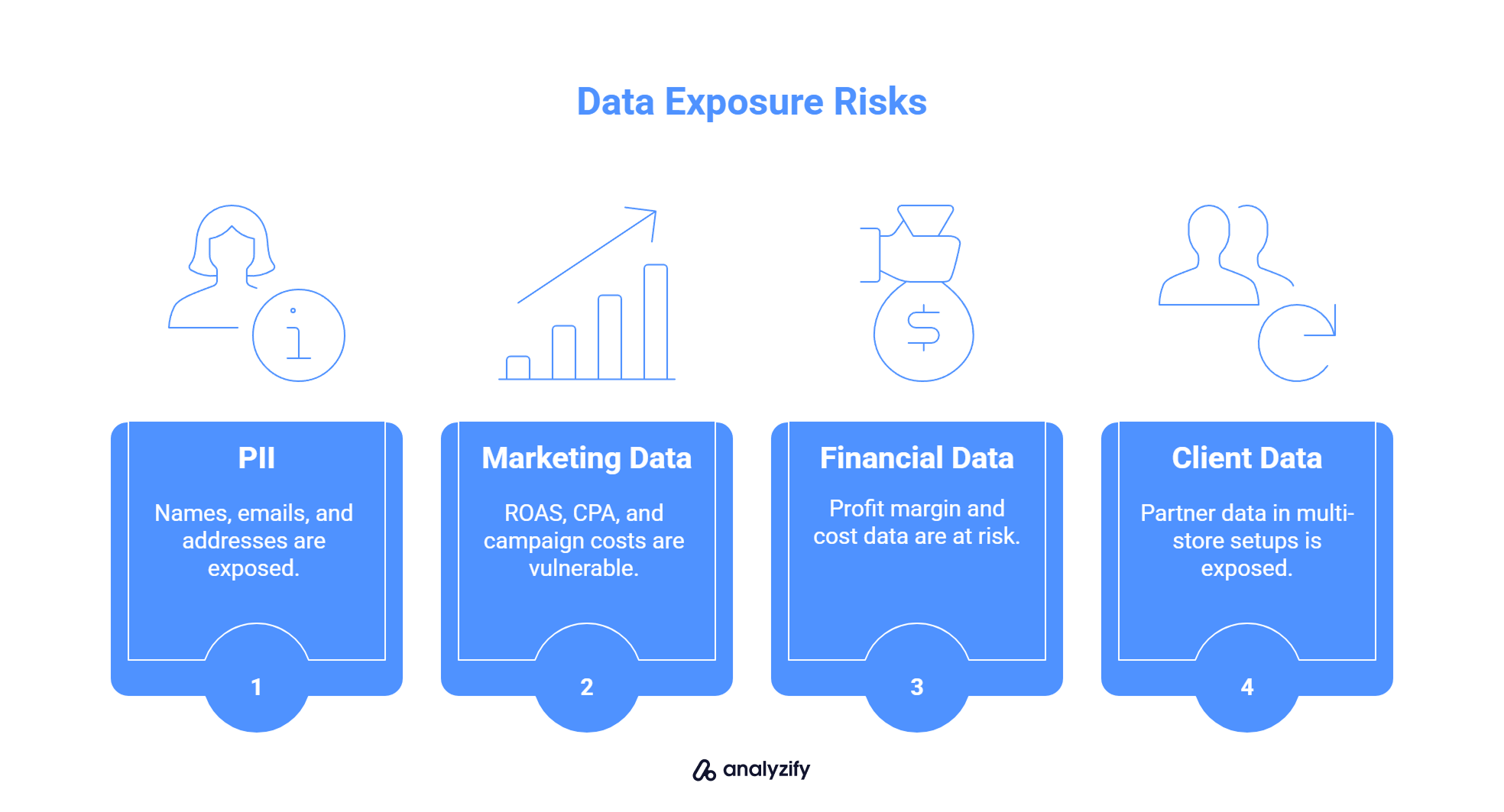
Personally Identifiable Information (PII) like names, emails, addresses
Marketing and ad spend performance such as ROAS, CPA, and campaign costs
Profit margin and cost data pulled from orders or product catalogs
Client or partner data in multi-store or multi-brand setups
When these are exposed to the wrong person, the result may not be a “breach” but the loss of trust, a privacy violation, or a GDPR compliance risk.
Why This Happens in Practice
The root cause usually isn’t malicious intent, but rather operational shortcuts or tool limitations:
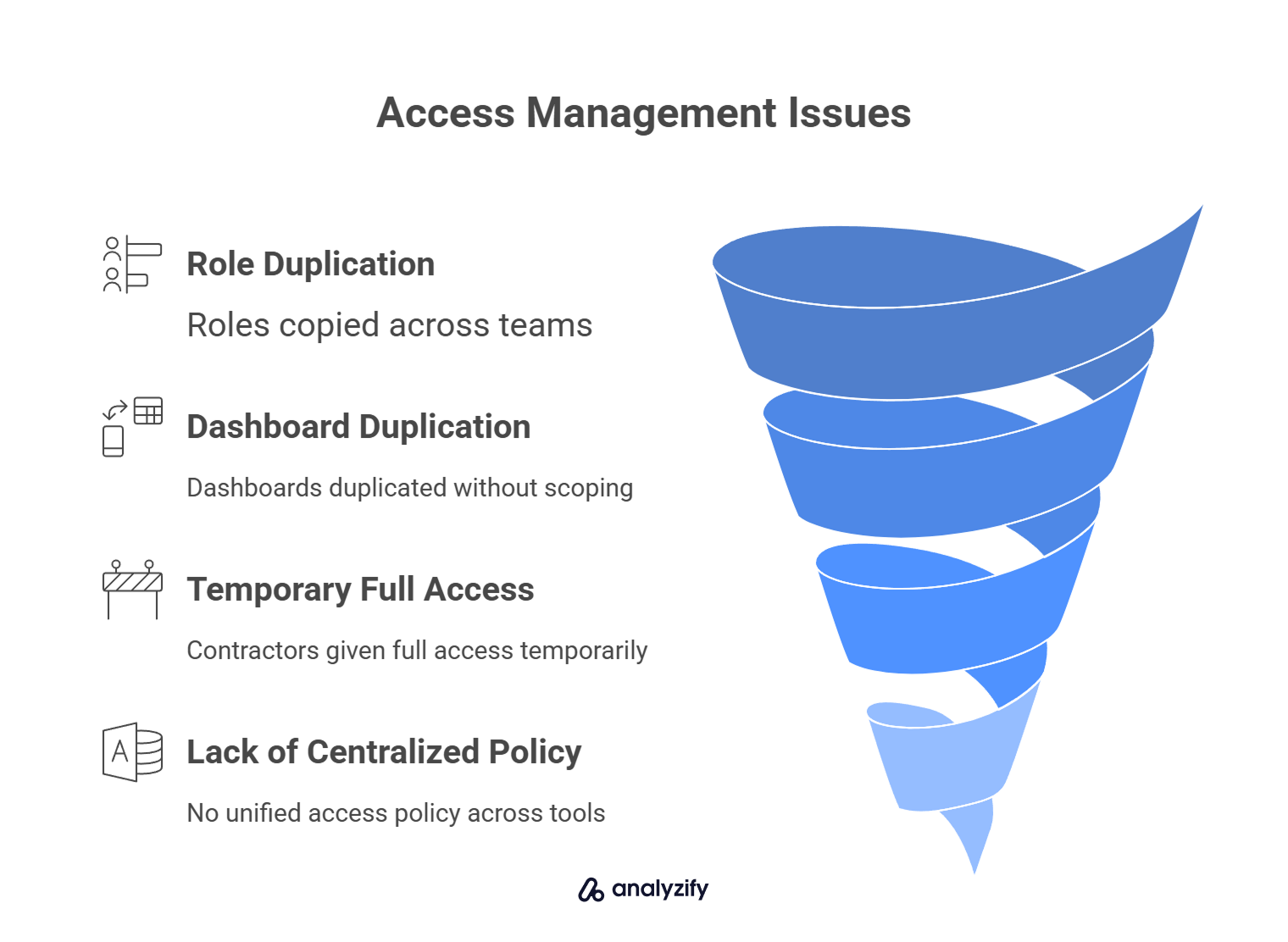
Roles are copied or reused across teams, giving more access than needed
Dashboards or reports are duplicated and not scoped per brand or client
Contractors or agency partners are given full access “just for now”
No centralized access policy is applied across tools like GA4, Looker, or BigQuery
This results in:
❌ Data visibility beyond team or brand boundaries
❌ Lack of logging for who viewed or queried sensitive data
❌ No way to simulate or test access logic before rollout
The Limits of Role-Based Access for Growing Teams
Most analytics and admin tools support Role-Based Access Control (RBAC) by default. This means users are assigned roles like admin, editor, or viewer, and those roles determine what they can access.
While RBAC works for simple setups, it breaks down quickly when your team, client base, or reporting needs start to grow.
Why RBAC Alone Is Not Enough
RBAC assumes that roles can be reused across users and teams. But in real-world e-commerce environments, access needs vary based on:
Which store, brand, or client a user is responsible for
Whether the person is internal staff, external agency, or temporary contractor
What regions or countries the data belongs to (especially with Shopify Markets)
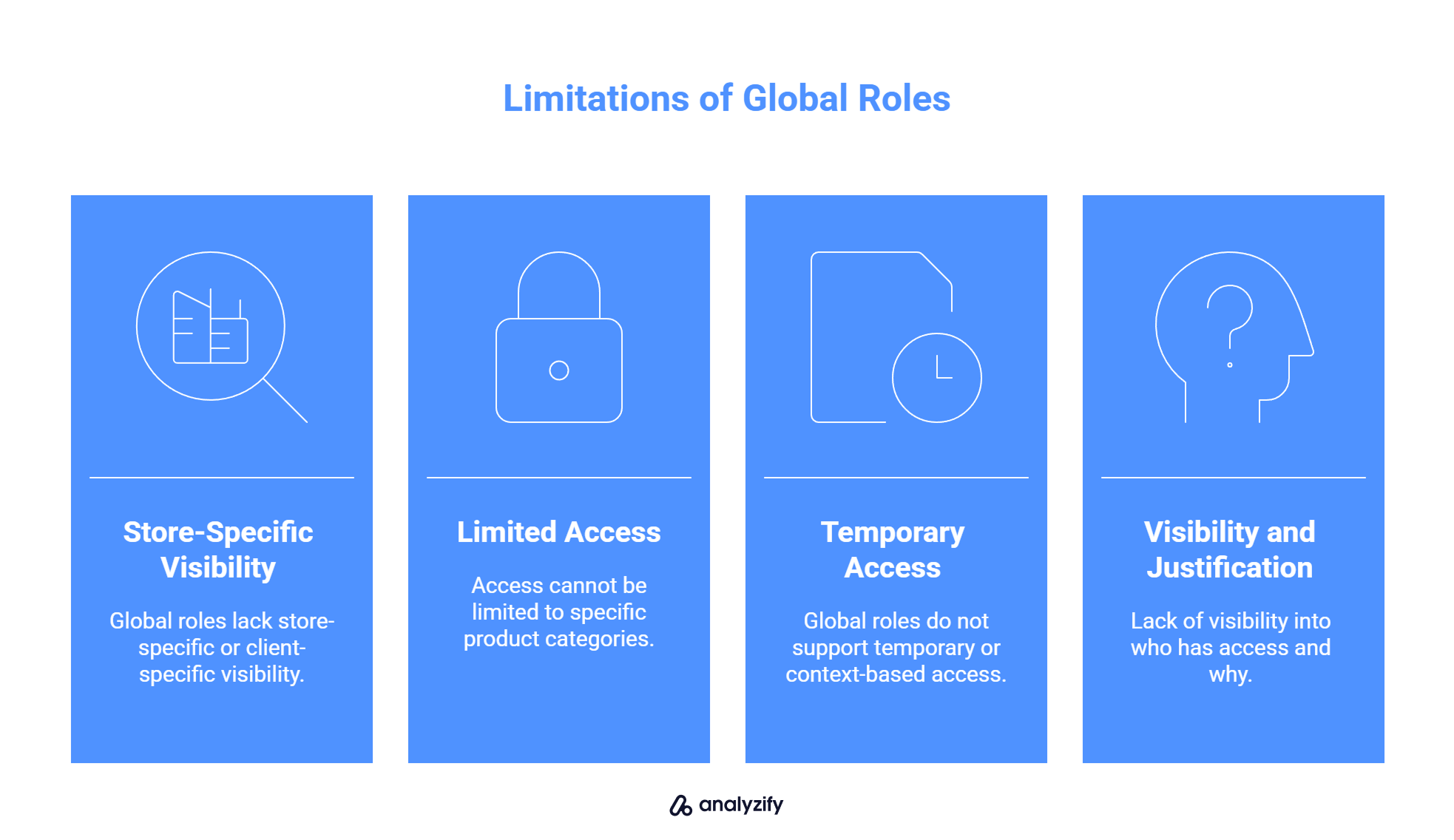
When access is managed only through global roles, you lose the ability to define:
✅ Store-specific or client-specific visibility
✅ Access limited to specific product categories, campaigns, or market segments
✅ Temporary access that expires or adjusts based on context
✅ Visibility into who has access to what and why
Common RBAC Issues in E-commerce Analytics Tools
When RBAC is used without scoping or context, it creates unnecessary overhead and increases risk. Teams often run into avoidable issues that slow down operations and weaken access security:
Role duplication: Dozens of near-identical roles are created just to reflect small differences, such as access per store or brand.
Over-permissioning: Users are granted broader access than needed to avoid administrative friction.
Poor visibility and patching: Admins lose track of who has access to what, and resort to spreadsheets or backend fixes to manage exceptions.
These patterns are common in e-commerce teams managing multiple clients, tools, or brands, and they signal the need for more advanced access control logic.
What’s Missing: Context and Boundaries
E-commerce teams often need attribute-based or tenant-aware access control. This means:
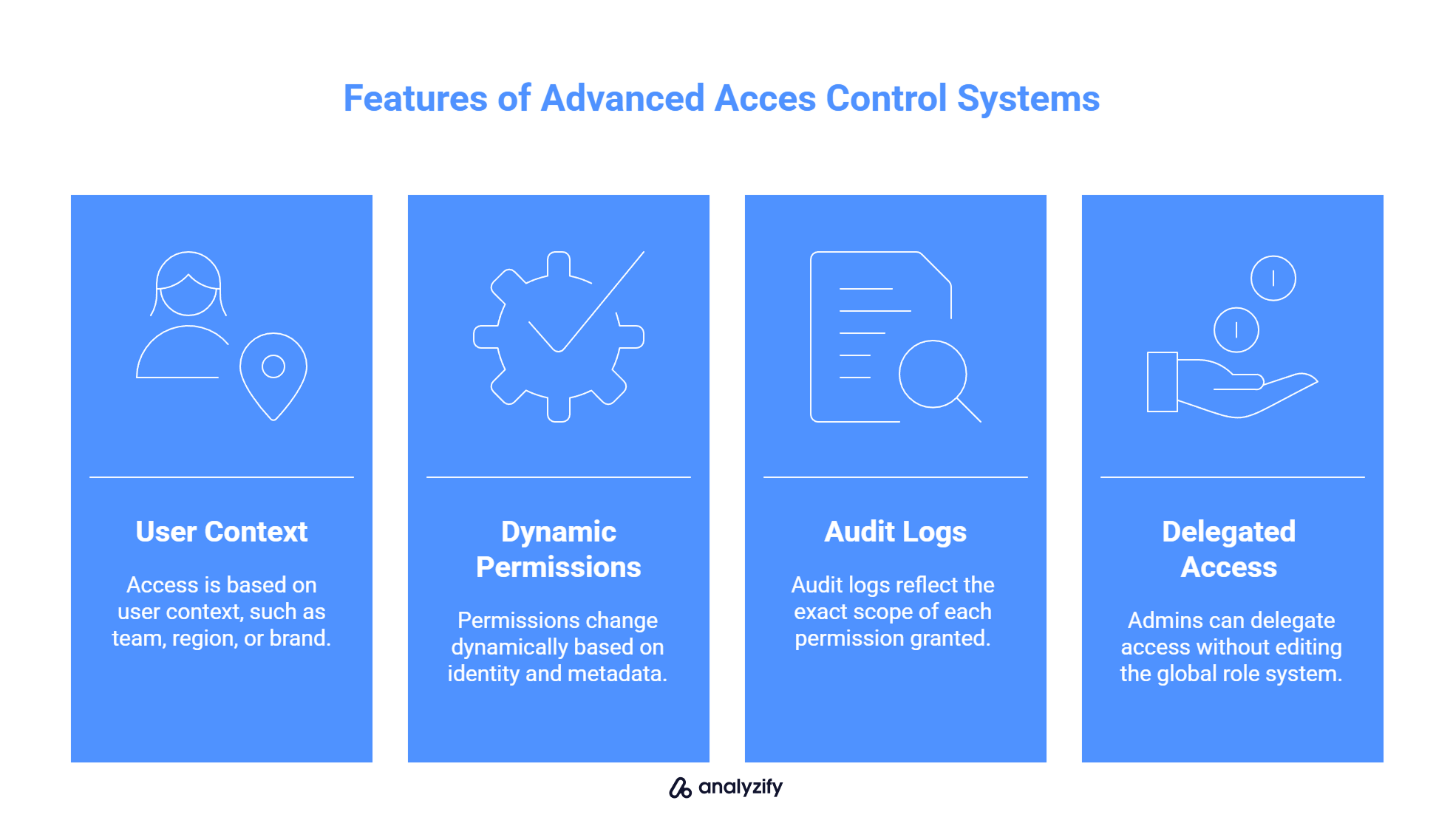
Access is based on user context (e.g. team, region, brand)
Permissions change dynamically based on identity and metadata
Audit logs reflect the exact scope of each permission
Admins can delegate access without editing the global role system
These capabilities go beyond traditional RBAC and require more advanced policy systems, especially when working with shared analytics stacks across multiple Shopify stores, regions, or client accounts.
What Secure Access Control Looks Like in E-commerce Data Tools
Once you recognize the risks of overexposed dashboards and the limits of basic role-based access, the next step is knowing what a strong access setup actually includes. In e-commerce, this means going beyond user roles and focusing on clear boundaries, traceability, and scalable delegation.
Essential Access Features for E-commerce Teams
To securely manage analytics tools like GA4, BigQuery, or internal dashboards, your access control system should support:
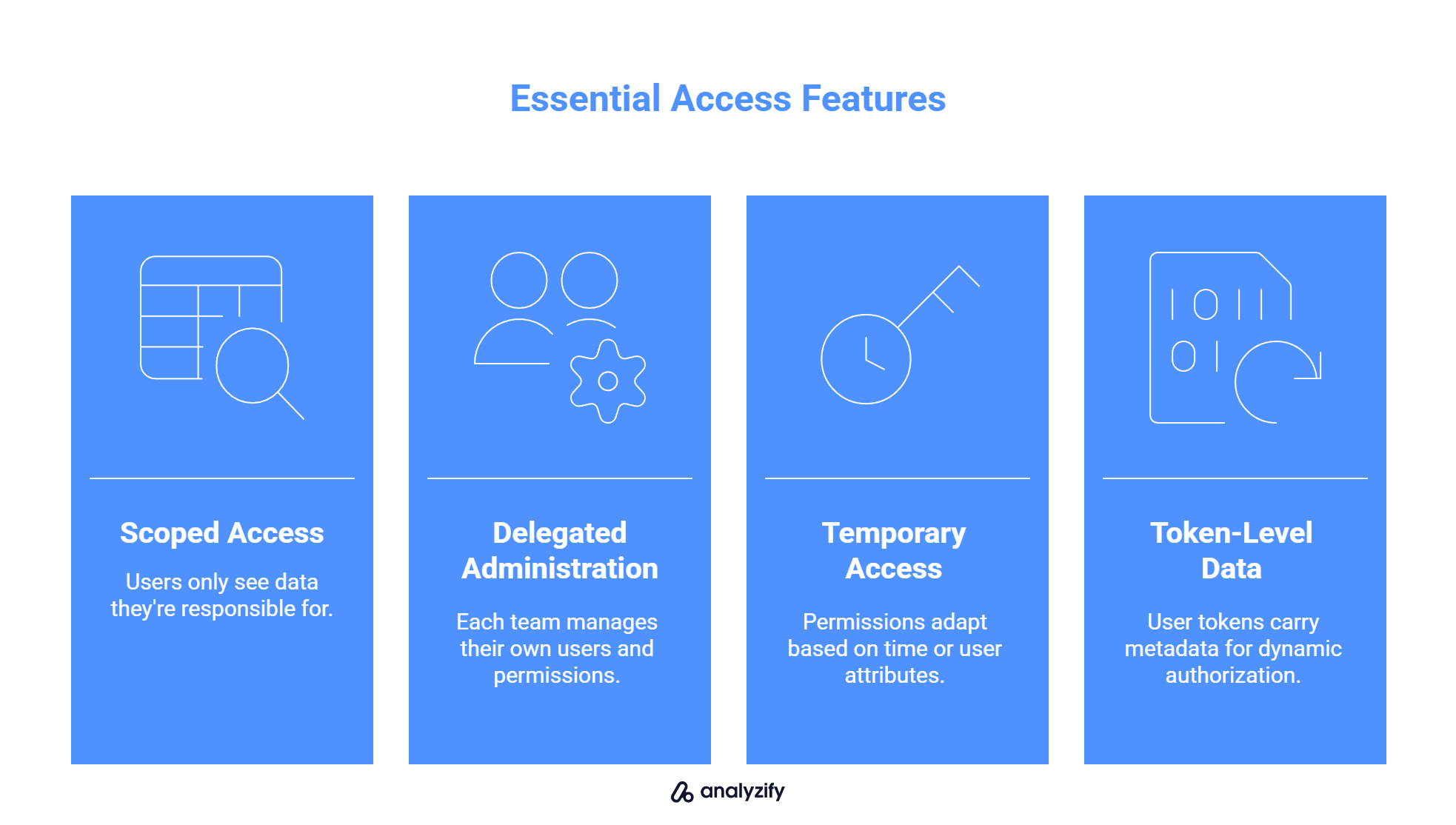
- Scoped access per client, brand, or store
Users should only see data tied to the store, project, or region they’re responsible for. This is critical for agencies or multi-store operators using shared reporting tools.
- Delegated administration
Each brand or client team should be able to manage their own users and permissions without needing global admin access. This prevents bottlenecks while maintaining boundaries.
- Temporary and context-aware access
Permissions should adapt based on time, session context, or user attributes. For example, a support team member might need limited access during a return request but nothing beyond that.
- Token-level organization data
User tokens should carry metadata like brand ID, department, or region to ensure authorization logic works dynamically without needing hardcoded rules.
Why Logging and Auditability Matter
A secure access setup must include visibility into how and why access decisions are made. That includes:
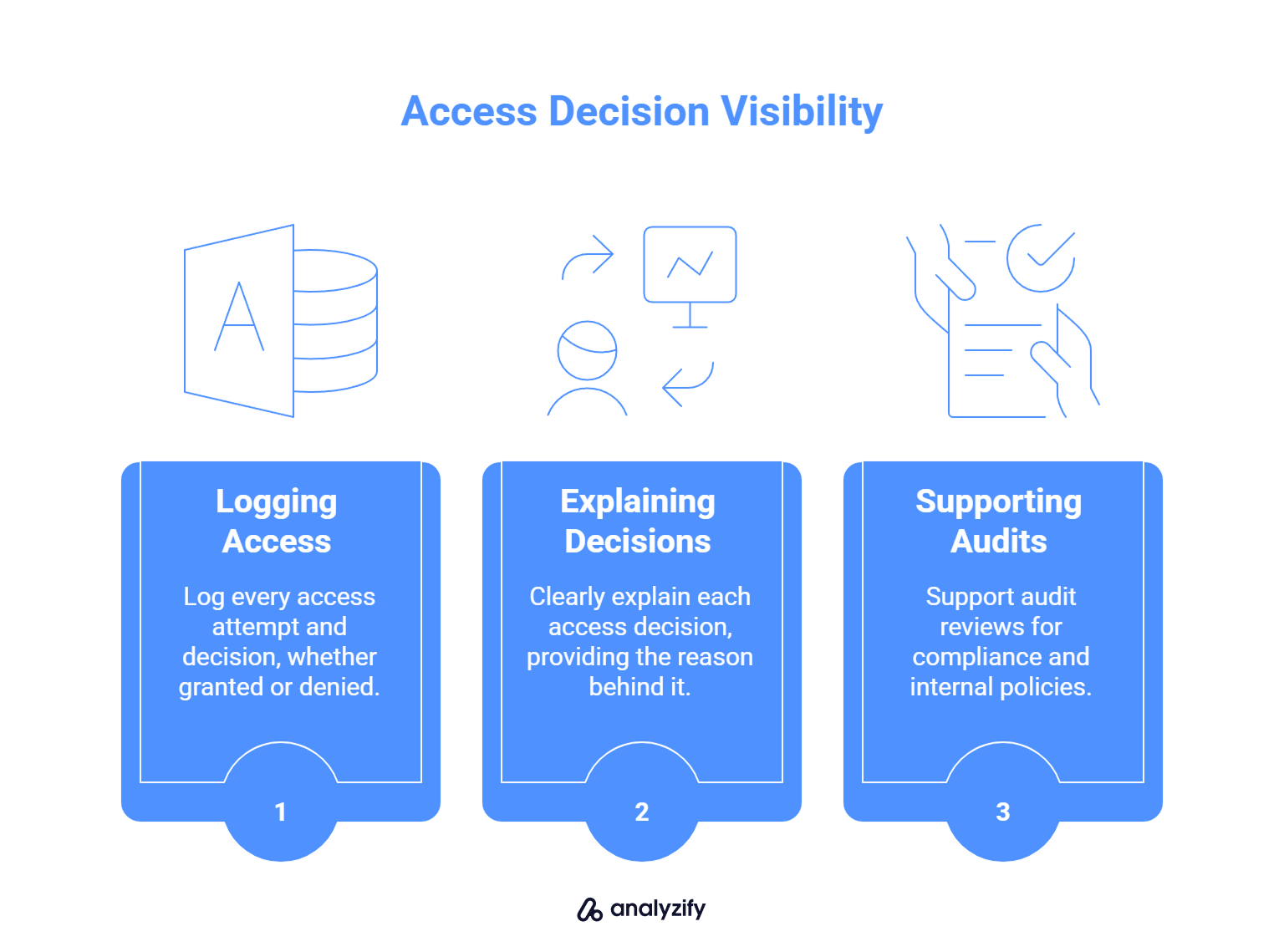
✅ Logging every access attempt and decision (granted or denied)
✅ Explaining each decision clearly not just “Access Denied” but why
✅ Supporting audit reviews for compliance and internal policies
Without these, access control becomes a black box, and mistakes stay hidden.
Why You Need Access Visibility in Analytics Platforms
Even if your access rules are well-defined, they don’t mean much if you can’t see how they’re applied. In e-commerce setups using GA4, BigQuery, or internal tools, access issues often come down to one simple problem: you don’t know why something was allowed or denied.
To prevent data mishandling and resolve permission issues quickly, teams need visibility into every access decision, not just error messages or manual reviews.
What Access Visibility Actually Means
Access visibility refers to the ability to trace, explain, and verify authorization decisions across your system. This includes:
Seeing who accessed what, and when
Understanding why an access request was denied
Reviewing the conditions that led to a decision, such as user attributes or request context
Comparing policy versions when behavior changes unexpectedly
This goes far beyond logging. It’s about making access behavior observable and testable, just like you would with application code.
Why Debugging Permissions Is Often Difficult
Most analytics tools don’t offer clear access feedback. Instead, teams face situations like:
A dashboard not loading without a clear reason
A new team member seeing data they shouldn’t
A permission change silently breaking a report
These issues are time-consuming to resolve because admins can’t simulate or test access scenarios before rollout, and logs, if they exist, are too vague to help.
The Role of Policy Simulation and Dry-Run Tools
A good access management system includes built-in tools to simulate access decisions using real or test data. These tools help you:
✅ Preview what a user can access before rolling out a policy
✅ Debug why a request was allowed or blocked, step by step
✅ Avoid deploying misconfigured rules into live environments
Without this kind of visibility, teams rely on trial-and-error, a risky and inefficient way to manage access at scale.
How Keymate Extends Keycloak for Secure E-commerce Access
If you already use Keycloak to manage identity and authentication, you’ve got the foundation in place. But Keycloak alone doesn’t cover the full range of access control needs that come up when you’re managing sensitive analytics data, multiple clients, or internal dashboards across e-commerce teams.
That’s where Keymate adds value. It builds directly on your existing Keycloak setup and gives you more control, better boundaries, and visibility into how access decisions are made.
Built for Teams Managing Sensitive Data Across Tools
Keymate is especially useful for e-commerce companies or agencies that work with tools like GA4, BigQuery, and Looker, where roles alone aren’t enough.
With Keymate, you can:
Define fine-grained access policies based on store, client, department, or user attributes
Implement tenant-level access scopes, so each brand or client only sees what they should
Delegate admin permissions per brand, without exposing global settings
Enrich tokens with structured context, such as region, business unit, or campaign
These features help keep your analytics environment clean and secure, even as your team or client list grows.
Access Observability and Simulation, Built In
Keymate also solves the visibility issues most teams run into when debugging access logic. Instead of guessing why something was denied or granted, you can simulate access scenarios and get detailed breakdowns of each decision.
You’ll be able to:
Run dry-run tests before rolling out new access policies
View real-time feedback explaining why a request was allowed or blocked
Audit every access attempt with full traceability including tenant, user, and decision context
This helps your team move faster while staying confident that internal dashboards, reports, and customer data are only available to the right people.
Before You Share That Dashboard: What to Prioritize in Access Control
If your team uses dashboards, analytics tools, or internal platforms to handle customer and business data, access control needs to be part of the setup, not an afterthought.
Before giving anyone access to GA4, BigQuery, Looker Studio, or your admin panel, it’s worth asking a few key questions:
Is access scoped to the right brand, client, or market?
Do we know exactly who can see which data, and why?
Can we simulate or test access before granting it?
Do we have logging in place to review and audit decisions?
If the answer to any of these is no, it’s a sign that your access strategy may need refinement.
Tools like Keymate are built to fill these gaps, especially for teams already using Keycloak. By enabling scoped permissions, delegated admin, and full policy observability, they help turn access control from a weak point into a manageable part of your analytics infrastructure.
































